Researchers from the Oregon State University College of Engineering have demonstrated that hackers can destabilize a power transmission grid by manipulating smart meters to generate an oscillation in electricity demand.
IEEE Access published the findings.
According to associate professor of electrical engineering and computer science Eduardo Cotilla-Sanchez, who led the project with graduate student Falah Alanazi, the study is important because understanding where a grid’s vulnerabilities lie and what they look like is the first step in designing protection mechanisms.
A smart meter is a digital device that uses a telecommunications connection to send electricity usage data to a local utility. The meters can assist clients with more deeply studying their power use, and they can likewise be utilized to shut down clients’ power, for example, on account of neglected charges from a distance.
“New technologies have been introduced to improve the efficiency and reliability of our aging electricity infrastructure. Communication systems, distribution automation, local control and protection systems, and advanced metering infrastructure have all been upgraded at the distribution level. The bad news is that the enhancements open up new avenues for assaulting the electricity grid.”
Eduardo Cotilla-Sanchez, associate professor of electrical engineering and computer science .
Power grid components can “trip” and shut off when demand, or load, is too high or problematic for any reason, similar to circuit breakers in a home panel. As a consequence, load is transferred to other parts of the grid network, which may also shut down, posing the risk of a domino effect that could result in a blackout.
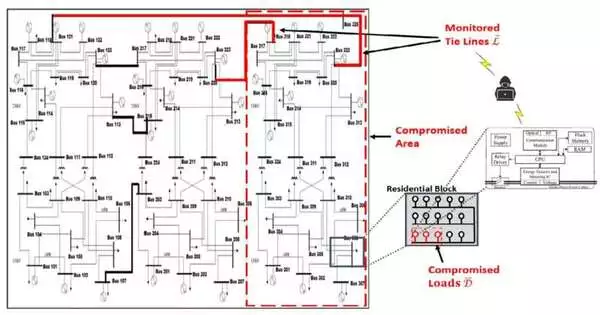
Using a model known as a time-domain grid protection simulator, the researchers in this study, led by associate professor Jinsub Kim of the OSU College of Engineering, demonstrated how transmission can be compromised by causing loads to oscillate in a regular pattern.
According to Cotilla-Sanchez, “new technologies have been introduced to make our aging electricity infrastructure more efficient and reliable.” Communication systems, distribution automation, local control and protection systems, and advanced metering infrastructure have all been upgraded at the distribution level. The bad news is that the upgrades also open up new ways to attack the power grid.
Hacking into the advanced metering infrastructure, or AMI for short, and controlling the smart meter switches to cause load oscillations is one type of attack made possible by new technologies.
Cotilla-Sanchez stated, “Imagine calling everyone you know and saying, ‘OK, at 6 p.m. we are all going to turn the lights on.'” Even if you got a few thousand people to do that, it wouldn’t cause much instability because the grid can handle pretty big changes in supply and demand. For instance, solar panels don’t produce electricity at the end of the day, and we can anticipate that and make up for it.
“Yet, assuming an individual were to somewhat facilitate an enormous number of shrewd meters to turn clients on and off at a specific recurrence, that would be an issue.”
He stated that someone would begin such an incident by conducting reconnaissance by “poking” a few locations within a grid and utilizing the information obtained to estimate the grid’s destabilizing oscillation frequency. The attacker would be prepared to launch an assault once they had identified which customer meters to turn on and off at that frequency, which is less than 1 hertz or cycle per second.
Additionally, an attack need not require as many meters to be effective.
Cotilla-Sanchez stated, “We juxtaposed our work with related recent grid studies and found that a well-crafted attack can cause grid instability with less than 2% of the system’s load.”
He added that, while the findings are troubling, they serve as a starting point for grid operators to develop countermeasures.
He stated, “For example, if they detect this type of oscillation on the load side, they could intentionally island the affected area and prevent the propagation of the instability to a broader area of the grid by taking lines A and B out of service.”
“Another solution, which could be complementary, could be to change the generation portfolio enough—for example, reduce some wind generation while increasing some hydro generation—so that the overall dynamic response is different from what the attack was designed to do and the impact won’t be big enough to tip the system.”
“Understanding the nature of possible attacks, I would say, is a good start,” he stated, “but understanding the nature of possible attacks will require additional research and development to serve as an effective mechanism of protection.”
More information: Falah Alanazi et al, Load Oscillating Attacks of Smart Grids: Vulnerability Analysis, IEEE Access (2023). DOI: 10.1109/ACCESS.2023.3266249