A group of specialists at the University of California, San Diego, has shown interestingly that the Bluetooth signals discharged continually by our cell phones have a one-of-a-kind unique mark that can be utilized to follow people’s developments.
Cell phones, including telephones, smartwatches, and wellness trackers, continually send signals, known as Bluetooth guides, at the pace of about 500 reference points per minute. These guides empower highlights like Apple’s “See as My” lost gadget following help; COVID-19 following applications; and integrating cell phones to different gadgets like remote headphones.
Earlier examination has shown that remote fingerprinting exists in WiFi and other remote advances. The basic understanding of the UC San Diego group was that this type of following should likewise be possible with Bluetooth, in a profoundly exact way.
“This is crucial since Bluetooth offers a more substantial threat in today’s society because it is a regular and steady wireless signal emitted by all of our personal mobile devices,”
Nishant Bhaskar, a Ph.D. student in the UC San Diego Department of Computer Science and Engineering
“This is significant in light of the fact that in this day and age, Bluetooth represents a more critical danger as it is a successive and consistent remote signal discharged from all our own cell phones,” said Nishant Bhaskar, a Ph.D. understudy in the UC San Diego Department of Computer Science and Engineering and one of the paper’s lead creators.
The group, which incorporates specialists from the Departments of Computer Science and Engineering and Electrical and Computer Engineering, introduced its discoveries at the IEEE Security and Privacy meeting in Oakland, Calif., on May 24, 2022.
All remote gadgets have little assembling defects in the equipment that are one of a kind to every gadget. These fingerprints are an unintentional result of the assembling system. These blemishes in Bluetooth equipment bring about one-of-a-kind twists, which can be utilized as a finger impression to follow a particular gadget. For Bluetooth, this would permit an aggressor to dodge hostile following strategies by, for example, continually changing the location a cell phone utilizes to interface with Internet organizations.
Following individual gadgets by means of Bluetooth isn’t direct. Earlier fingerprinting methods that worked for WiFi depended on the way that WiFi signals incorporate a long-known succession, called the introduction. Be that as it may, prefaces for Bluetooth reference point signals are very short.
“The brief term gives an off-base unique mark, making earlier methods not helpful for Bluetooth following,” said Hadi Givehchian, a UC San Diego software engineering Ph.D. understudy and a lead creator on the paper.
All things being equal, the specialists planned another strategy that doesn’t depend on the prelude yet takes a gander at the entire Bluetooth signal. They devised a calculation that gauges two distinct qualities found in Bluetooth signals. These qualities change in view of the imperfections in the Bluetooth equipment, giving analysts the gadget’s exceptionally unique finger impression.
Genuine tests
The scientists assessed their following strategy through a few true trials. In the primary trial, they saw that 40% of 162 cell phones found in open regions, for instance, cafés, were particularly recognizable. Then, they increased the trial and noticed 647 cell phones in a public lobby across two days. The group saw that 47% of these gadgets had one-of-a-kind fingerprints. At last, the specialists showed a real follow-up assault by fingerprinting and following a cell phone possessed by a volunteer as they strolled all through their home.
Challenges
Despite the fact that their findings are disturbing, the experts also discovered a few issues that an aggressor will consider.Changes in surrounding temperature, for instance, can adjust the Bluetooth finger impression. Certain gadgets additionally convey Bluetooth messages with various levels of force, and this influences the distance at which these gadgets can be followed.
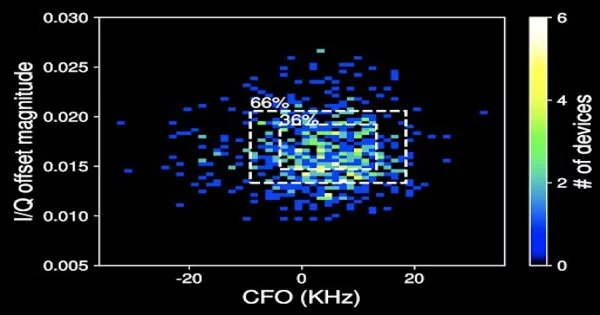
Scientists had the option to identify interesting fingerprints for 47% of 647 gadgets.
Specialists likewise note that their technique requires an aggressor to have a serious level of mastery, so being a general danger to the public today is improbable.
Regardless of the difficulties, the scientists found that Bluetooth following is reasonably doable for an enormous number of gadgets. It also doesn’t need modern hardware: the assault can be performed with gear that costs under $200.
Arrangements and following stages
So how could the issue be fixed? At a very basic level, Bluetooth equipment would need to be updated and supplanted. However, the analysts accept that other, simpler arrangements can be found. The group is presently working on a method for concealing the Bluetooth fingerprints through computerized signal handling in the Bluetooth gadget firmware.
Specialists are likewise investigating whether the strategy they created could be applied to different sorts of gadgets. “Each type of correspondence today is remote and in danger,” said Dinesh Bharadia, a teacher in the UC San Diego Department of Electrical and Computer Engineering and one of the paper’s senior creators. “We are attempting to assemble equipment-level protection for expected assaults.”
Analysts found that simply handicapping Bluetooth may not be guaranteed to prevent all telephones from radiating Bluetooth guides. For instance, reference points are as yet radiated while switching off Bluetooth from the control community on the home screen of some Apple gadgets. “Apparently, the main thing that most certainly stops Bluetooth reference points is switching off your telephone,” Bhaskar said.
Analysts are mindful so as to say that despite the fact that they can follow individual gadgets, they can’t get any data about the gadgets’ proprietors. The review was checked on by the grounds’ Internal Review Board and grounds counsel.
“The gadgets are actually under a microscope,” said Aaron Schulman, a UC San Diego software engineering professor and one of the paper’s senior authors.
More information: Evaluating physical-layer BLE location tracking attacks on mobile devices, IEEE Security & Privacy conference in Oakland, Calif., May 24, 2022. PDF: cseweb.ucsd.edu/~schulman/docs … nd22-bletracking.pdf