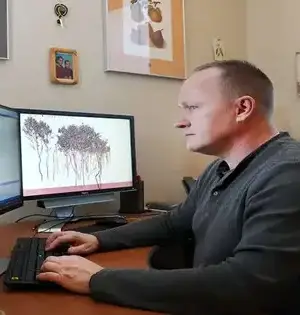
An examination group from Purdue College's Division of Software Engineering and Foundation for Computerized Ranger Service, with partner Sören Pirk at Kiel College in Germany, has found that man-made consciousness can reenact tree development and shape. The DNA atom encodes both tree shape and natural reaction in one little, subcellular bundle. In work propelled by DNA, Bedrich Benes, a teacher of software engineering, and his partners created novel artificial intelligence models that pack the data expected for encoding tree structure into a megabyte-sized brain model. In the wake of preparing, the computer-based intelligence models encode the nearby improvement of trees
Computer Sciences
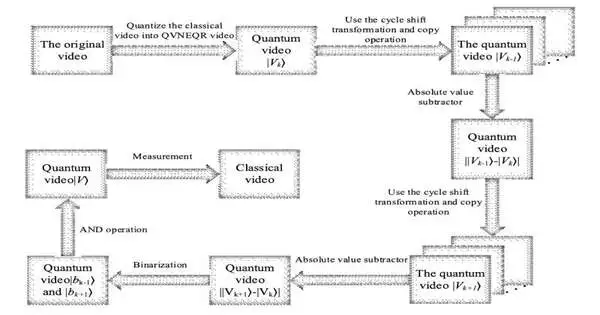
PC vision calculations have progressively progressed over the course of the last many years, empowering the improvement of refined advances to screen explicit conditions, identify objects of interest in video film, and uncover dubious exercises in CCTV accounts. A portion of these calculations are explicitly intended to identify and disconnect moving items or individuals of interest in a video, an errand known as moving objective division. While a few regular calculations for moving objective division achieved promising outcomes, the greater part of them performed ineffectively continuously (i.e., while examining recordings that were not pre-recorded yet are being caught right now).
Despite constant advancements, quantum computers are still noisy and prone to errors, which produce ambiguous or incorrect responses. They won't actually surpass today's "classical" supercomputers for at least five or ten years, according to scientists, because of the mistakes that plague entangled quantum bits, or qubits. However, a recent study demonstrates that, even in the absence of effective error correction, there are strategies to reduce faults that might make quantum computers usable right now. Researchers at IBM Quantum in New York and their collaborators at the University of California, Berkeley, and Lawrence Berkeley National Laboratory report today (June 14) in
The world may undergo a transformation thanks to quantum computing. It promises to be considerably faster for certain and important activities than the zero-or-one binary technology that powers today's equipment, from supercomputers in research labs to smartphones in our pockets. However, creating a reliable network of qubits, or quantum bits, to store information, access it, and carry out computations, is essential for creating quantum computers. Yet the qubit platforms unveiled to date have a common problem: They tend to be delicate and vulnerable to outside disturbances. Even a stray photon can cause trouble. The ultimate answer to this problem might
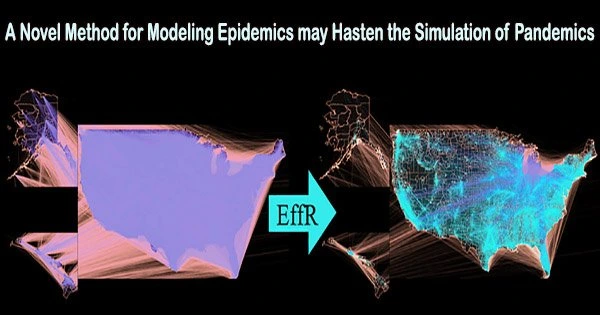
It can take weeks or even months to run the simulations needed to predict how a pandemic of this magnitude will spread. A new method for epidemic modeling is presented in a recent paper published in PLOS Computational Biology, and it could significantly speed up the procedure. The study employs sparsification, a technique from computer science and graph theory, to determine which connections in a network are crucial for the transmission of disease. The scientists discovered they could cut the calculation time for simulating the transmission of diseases over extremely complex social networks by 90% or more by concentrating on
Modern technology could undergo a revolution thanks to quantum research thanks to more effective computers, communications, and sensors. However, there are still difficulties in realizing these technological objectives, such as how to properly control information in quantum systems. In a paper published in Nature Physics, a group of researchers from the University of Rochester, including John Nichol, an associate professor of physics, outlines a new method for controlling electron spin in silicon quantum dots tiny, nanoscale semiconductors with remarkable properties as way to manipulate information in a quantum system. “The results of the study provide a promising new mechanism for
Using the fastest supercomputer in Japan, a study team from Nagoya University was able to recreate air turbulence that occurs in the vicinity of Tokyo on clear days. For the purpose of developing a more precise forecasting model, they later contrasted their findings with flying data. The research was reported in the journal Geophysical Research Letters. Although air turbulence is typically linked with inclement weather, it can occur on clear, sunny days as well. These turbulent air movements, known as clear air turbulence (CAT), can happen even when there are no apparent clouds or other meteorological disturbances. Although the precise
In research using ChatGPT, it was discovered that the artificial intelligence tool properly answered fewer than half of the test questions from a study guide frequently used by doctors in order to become certified in ophthalmology. In the study, which was headed by St. Michael's Hospital, a Unity Health Toronto facility, and published in JAMA Ophthalmology, it was discovered that when it was first used in January 2023, ChatGPT correctly answered 46% of questions. One month later, when researchers repeated the test, ChatGPT received results that were more than 10% higher. The potential of AI in medicine and exam preparation
Real-time diagnostic and disease-monitoring technologies require sophisticated systems for the detection of biomarker molecules, such as DNA or proteins, that signal the existence of a disease. The work of UC Santa Cruz's eminent electrical and computer engineering professor Holger Schmidt and his team has long been focused on creating novel, extremely sensitive devices called optofluidic chips to detect biomarkers. Schmidt's graduate student Vahid Ganjalizadeh led an effort to use machine learning to enhance their systems by improving its ability to accurately classify biomarkers. According to a recent publication published in Nature Scientific Reports, the deep neural network he designed can
Once upon a time, we figured the most horrendously terrible things that could occur during a Zoom gathering were unintentionally leaving the mouthpiece on while reviling out your feline, hearing somebody wheezing during your heavenly summation of your most recent undertaking, or rising up to hurry to the kitchen while failing to remember you have no jeans on. In any case, a group of English scientists revealed last week that programmers sitting close by in a café can get and recognize keystrokes over a Zoom call. It is the most recent variety of lifting information in light of the actual