Scientists at the College of Oxford, as a team with global specialists, have distributed another concentrate in Nature Machine Knowledge, resolving the complex moral issues encompassing liability regarding yields created by enormous language models (LLMs). The study reveals that, in contrast to traditional AI responsibility debates that primarily focused on negative consequences, LLMs like ChatGPT pose crucial questions regarding the attribution of credit and rights for useful text generation. "LLMs like ChatGPT bring about an urgent need for an update in our concept of responsibility," say the study's co-first authors, Sebastian Porsdam Mann and Brian D. Earp. "We recommend that
Computer Sciences
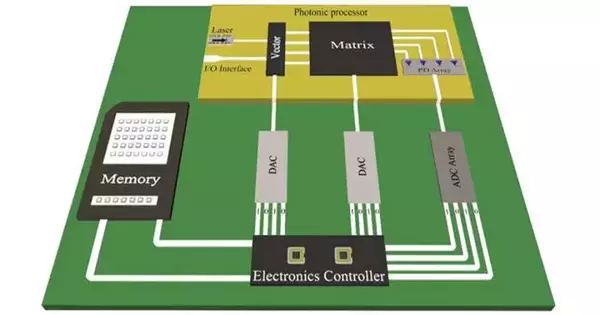
A new light-based computing method that uses a photonic integrated circuit to save energy for cryptocurrency and blockchain applications has been developed by researchers. Mining cryptographic forms of money like Bitcoin — a course of confirming exchanges and adding new digital currency to the blockchain — consumes up to 1% of the world's energy. As applications based on cryptocurrencies and blockchain technology become more commonplace, it is anticipated that energy consumption will rise. Cryptographic forms of money are advanced monetary standards made using encryption calculations. A blockchain—a type of digital ledger that records information like transactions in a way that
2019 will see the MIT Ph. D. Ajay Brahmakshatriya, a student, came up with a straightforward but challenging objective. He wanted to make it possible for people with expertise in a specific field—like climate modeling, bioinformatics, or architecture—to write their own programming languages, known as domain-specific languages (or DSLs), even if they had little to no experience doing so. Brahmakshatriya wanted these languages to include all the auxiliary functions people would need to comfortably use them, including tools for debugging. He was a member of the research team led by MIT Professor Saman Amarasinghe in the Institute's Computer Science and
This week saw a significant advancement in meta with the release of a model that can recognize and isolate objects in an image even if it has never seen them before. A pre-print server article on arXiv introduces and describes the technology. The AI tool represents a significant advancement in one of technology's more difficult problems: enabling computers to recognize and understand the components of a previously unseen image and isolate them for user interaction. It brings to mind a theory put forth by Robert O., the previous leader of the National Security Commission on Artificial Intelligence. As one employee
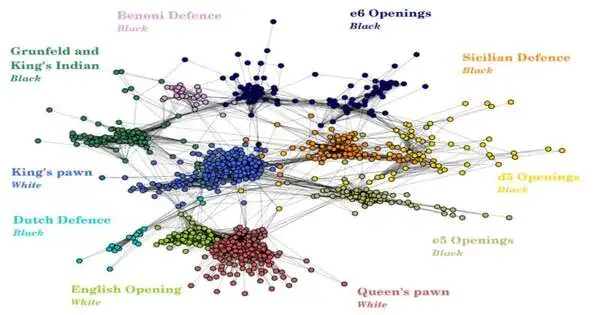
Complexity Science Hub and Centro Ricerche Enrico Fermi (CREF) researchers examined the similarities between various chess openings using actual data from an online chess platform. They created a new classification technique to support the existing classification based on these similarities. Giordano De Marzo of the Complexity Science Hub and the Centro Ricerche Enrico Fermi (CREF) explains, "To find out how similar chess openings actually are to each other—meaning in real game behavior—we drew on the wisdom of the crowd. In order to determine who plays which opening games, the researchers examined 3,746,135 chess games, 18,253 players, and 988 different openings
Two of the most well-known artificial intelligence techniques, deep neural networks and vector-symbolic models, have recently been combined by researchers at IBM Research Zürich and ETH Zürich to form a new architecture. Their architecture, which was published in Nature Machine Intelligence, could get around both of these methods' drawbacks, solving progressive matrices and other reasoning problems more successfully. One of the researchers who conducted the study, Abbas Rahimi, told Tech Xplore that their most recent paper was "based on our earlier research works aimed at augmenting and enhancing neural networks with the powerful machinery of vector-symbolic architectures (VSAs)". "This combination
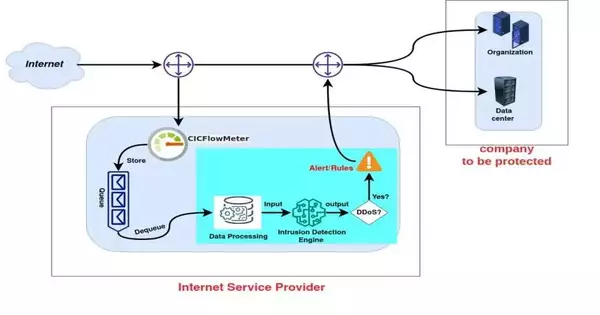
Cybercriminals are thinking of increasingly canny ways of upsetting web-based administrations, accessing touchy information, or crashing web clients' gadgets. A digital assault that has become extremely normal over the course of the last many years is the purported Conveyed Forswearing of Administration (DDoS) assault. This sort of assault includes a progression of gadgets associated with the web, which are by and large alluded to as a "botnet." This "bunch" of associated gadgets is then used to flood an objective server or site with "counterfeit" traffic, upsetting its activity and blocking it off to genuine clients. Organizations and different clients generally
MIT researchers have created an expanded reality headset that provides the wearer with X-beam vision. The headset joins PC vision and remote insight to naturally find a particular thing that is stowed away from view, maybe inside a container or under a heap, and afterward guide the client to recover it. The framework uses radio frequency (RF) signals, which can go through normal materials like cardboard boxes, plastic compartments, or wooden dividers, to find stowed-away things that have been named with RFID labels, which reflect signals sent by an RF receiving wire. The headset coordinates the wearer as they stroll
Heat causes blunders in the qubits that are the building blocks of a quantum computer, so quantum frameworks are normally kept inside coolers that keep the temperature simply above outright zero (-459 degrees Fahrenheit). Yet, quantum PCs need to communicate with gadgets outside the cooler, in a room-temperature climate. The metal links that connect these gadgets carry heat into the fridge, which needs to work much harder and attract additional ability to keep the framework cold. Besides, more qubits require more links, so the size of a quantum framework is restricted by how much intensity the cooler can eliminate. To
"Everything is numbers," admitted Pythagoras. Today, after 25 centuries, polynomial math and math are everywhere in our lives, regardless of whether we see them. Because innovative development considers equal handling of large amounts of tasks, the Cambrian-like blast of man-made reasoning (simulated intelligence) brought numbers much closer to all of us. Logically, tasks between scalars (numbers) were parallelized into activities among vectors, and hence, grids. Increase between grids is currently the most investment-demanding activity of modern man-made intelligence computational frameworks.A method called "tiled grid duplication" (TMM) assists with speeding up calculation by decaying network tasks into more modest tiles that