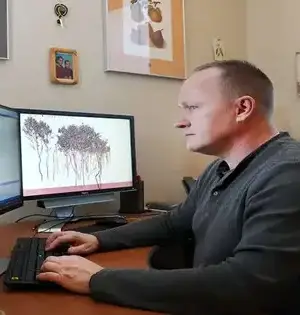
An easy-to-use set of physical gestures that attendees in online group video meetings can utilize to enhance their meeting experience has been designed and tested by researchers. Paul D. Hills of University College London, U.K., and colleagues from University College London and the University of Exeter, U.K., present the technique, which they call Video Meeting Signals (VMS™), in the open-access journal PLOS ONE on August 3, 2022. Online video conferencing has been a helpful resource for business, education, and social contacts throughout the COVID-19 pandemic. It has also been linked to weariness, poor communication, and poor mental health. Hills created
Computer Sciences
Game engines were initially created to create fictional worlds for entertainment purposes. However, these same engines can be used to create digital twins, which are exact replicas of genuine worlds. Researchers from Osaka University have discovered a way to train deep learning models that can quickly scan photos of real cities and precisely differentiate the buildings that appear in them using the images that were automatically created by digital city twins. A deep learning neural network called a convolutional neural network is made for processing structured data sets like photographs. The way tasks like architectural segmentation are carried out has
Many commonly used cryptosystems could be quickly cracked by quick algorithms on quantum computers, requiring more creative approaches to digital security. In a recent study, a group of researchers created a stream cipher using three primitives for cryptography that were each based on a different mathematical model of chaos. The resulting cryptographic method paves the way for secure digital communications in the post-quantum age and is resistant to attacks from powerful quantum computers. It can also be applied to low-cost machines. While for most of us cryptographic systems are things that just run "under the hood," they are an essential
According to a study by Johns Hopkins Medicine, the Kennedy Krieger Institute, and the University of Maryland, new pose estimate software has the potential to help neurologists and their patients gather crucial clinical data using basic equipment like smartphones and tablets. Artificial intelligence known as "human posture estimation" uses straightforward photos or videos to automatically recognize and name particular landmarks on the human body, such as elbows, and fingers. Neurologists frequently ask patients to make certain repeated motions, like tapping their fingers or opening and closing their hands, in order to quantify the speed, rhythm, and range of their motor
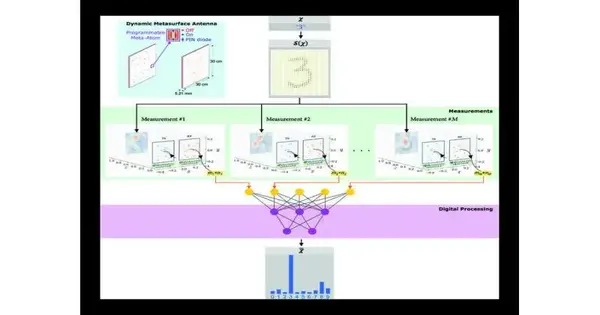
Detecting frameworks are becoming increasingly common in many aspects of our lives, including medical care, autonomous vehicles, and touchless human-PC interaction.Be that as it may, these frameworks frequently need knowledge: they will quite often accumulate all suitable data, regardless of whether it is important. This can lead not exclusively to protection encroachments, but also to sitting around, energy consumption, and computational assets during information handling. To resolve this issue, specialists from the French CNRS thought of an idea for smart electromagnetic detection that utilizes AI procedures to create learned brightening designs in order to pre-select important subtleties during the estimation
Social media networks generally put the majority of users in the backseat while battling the spread of false information. Platforms frequently employ machine-learning algorithms or human fact-checkers to alert consumers to information that is inaccurate or misleading. “Just because this is the status quo doesn't mean it is the correct way or the only way to do it,” says Farnaz Jahanbakhsh, a graduate student in MIT's Computer Science and Artificial Intelligence Laboratory (CSAIL). She ran a study with her colleagues in which they gave social media users that authority instead. First, they conducted a poll to find out how people
Practical attractive reverberation imaging (fMRI), which estimates changes in blood stream all through the mind, has been involved over the recent a long time for various applications, including "useful life systems" — an approach to figuring out which cerebrum regions are turned on when an individual does a specific errand. fMRI has been utilized to see individuals' minds while they're doing a wide range of things — resolving numerical questions, learning unknown dialects, playing chess, making do on the piano, doing crossword riddles, and in any event, staring at the Programs like "Check Your Energy." One pursuit that is gotten
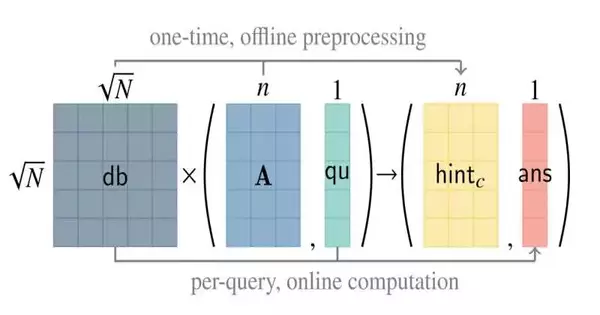
Looking through the web can uncover data a client would prefer to keep hidden. For example, when somebody looks into clinical side effects on the web, they could uncover their ailments through research, an internet-based clinical data set like WebMD, and maybe many of these organizations' sponsors and colleagues. For a long time, scientists have been developing procedures that allow clients to search for and recover data from a data set invisibly, but these techniques are far too late to be successfully used in the future. MIT specialists have now developed a plan for private data recovery that is multiple
As of late, profound learning strategies have accomplished surprising outcomes in various language and picture handling tasks. This incorporates visual discourse acknowledgment (VSR), which involves recognizing the substance of discourse exclusively by dissecting a speaker's lip movements. While some profound learning calculations have accomplished exceptionally encouraging outcomes on VSR errands, they were essentially prepared to identify discourse in English, as most existing preparation datasets just incorporate English discourse. This restricts their potential client base to individuals who live or work in English-speaking settings. Scientists at Magnificent School London recently developed another model that can handle VSR tasks in various dialects.This
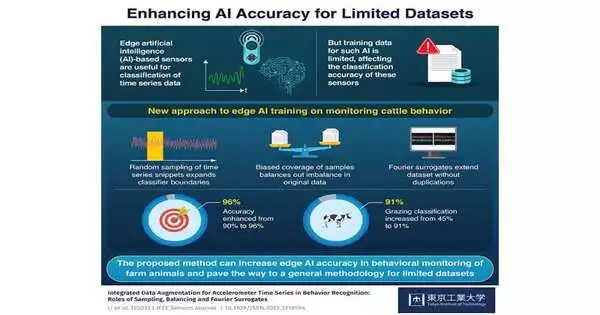
Engineers at the Tokyo Foundation for Innovation (Tokyo Tech) have shown a straightforward computational methodology for further developing the way man-made reasoning classifiers, like brain organizations, can be prepared in view of restricted measures of sensor information. The emerging Web of Things applications frequently necessitate cutting-edge gadgets that can reliably group behaviors and circumstances based on time series. Nonetheless, gathering information is time-consuming and costly.The proposed approach vows to considerably improve the nature of classifier preparation at basically no additional expense. Lately, the possibility of having immense quantities of Web of Things (IoT) sensors discreetly and steadily checking endless parts