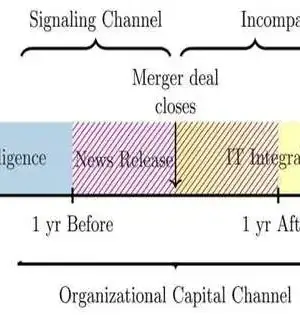
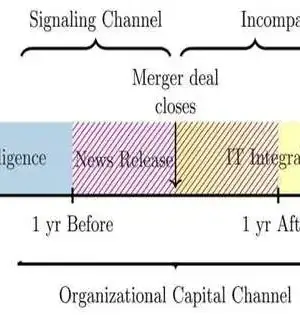
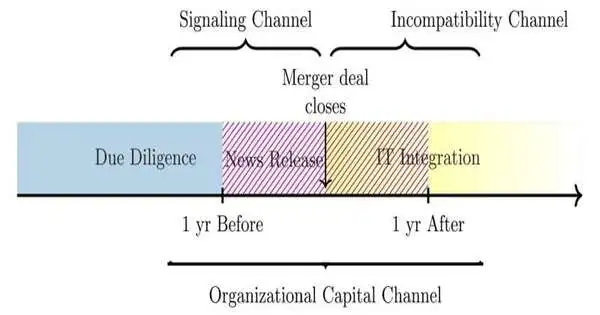
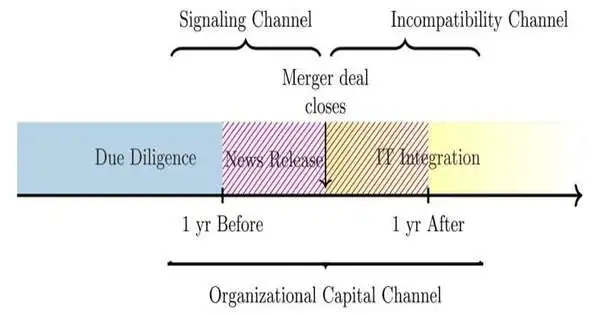
The period during and after clinic consolidations and acquisitions is a particularly weak time for patient information whenever the opportunity of a network protection break dramatically increases, as per research by a College of Texas at Dallas doctoral understudy. Simply the declaration of a consolidation is sufficient to set off expanded information breaks, said Nan Forbearing, a Ph.D. up-and-comer in financial aspects in the School of Monetary, Political, and Strategy Sciences. Lenient examined emergency clinic consolidation records and chronicled information break revealing from the Division of Wellbeing and Human Administrations from 2010 to 2022 and found that in a two-year
Security
The period during and after medical clinic consolidations and acquisitions is a particularly weak time for patient information whenever the opportunity of a network safety break dramatically increases, as per research by a College of Texas at Dallas doctoral understudy. Simply the declaration of a consolidation is sufficient to set off expanded information breaks, said Nan Forebearing, a Ph.D. competitor in financial matters in the School of Monetary, Political, and Strategy Sciences. Fore bearing examined emergency clinic consolidation records and filed information break revealing from the Branch of Wellbeing and Human Administrations from 2010 to 2022 and found that in
Policing across the country consistently sells things that are held onto in criminal examinations or are unclaimed from lost-and-tracked-down inventories. Automobiles, jewelry, watches, and mobile phones are just a few of the items that end up at online auction houses. Individuals searching for a deal can offer on cellphones in mass, grabbing up handfuls at absolute bottom costs for parts or different purposes. In the end, this makes money for the police departments, which is a win-win situation for everyone involved. Or, on the other hand, is it? A new report by College of Maryland security specialists found that large
Imagine watching a movie about a rogue employee who compromises security at a company that inserts chips into half of the computers on the planet. They enslave the world by installing Trojans in systems all over the world. According to Rajat Kumar, a Ph.D., this is not unfathomable. D. student working in Yehia Massoud's lab at KAUST He confirms that a single company currently provides more than half of the chips in use worldwide, including nearly all of the most sophisticated chips. The group led by Massoud investigates cutting-edge technology that might strengthen chip security. Multifunctional logic gates have been