Another technique that could consequently distinguish and kill cyberattacks on our workstations, PCs, and brilliant gadgets in less than a second has been developed by specialists at Cardiff University.
Using artificial consciousness in an ingenious way, the strategy has been shown to effectively prevent up to 92 percent of records on a PC from being corrupted, with a piece of malware being cleared out in only 0.3 seconds on average.
Distributing their discoveries in the journal Security and Communications Networks, the group says this is the principal exhibit of a strategy that can both identify and eliminate malignant programming progressively, which could change ways to deal with current online protection and stay away from cases like, for example, the new WannaCry cyberattack that hit the NHS in 2017.
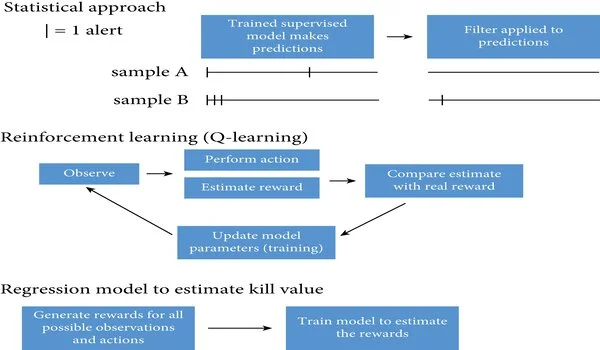
The new methodology, created as a team with Airbus, depends on checking and foreseeing the ways of behaving of malware instead of more customary antivirus approaches that break down what a piece of malware resembles.
“Customary antivirus programming will take a gander at the code construction of a piece of malware and say ‘better believe it, that looks natural’,” co-creator of the review Professor Pete Burnap makes sense of.
However, the issue is that malware creators will simply hack and change the code, so the following day the code appears to be unique and isn’t distinguished by the antivirus programming. We need to know how a piece of malware acts, so when it begins going after a framework, such as opening a port, making an interaction or downloading a few pieces of information in a specific request, it will abandon a unique finger impression, which we can then use to develop a conduct profile.
Via preparing PCs to run reproductions of unambiguous bits of malware, it is feasible to make an extremely fast expectation in under a moment of how the malware will act sometime later.
When a piece of programming is hailed as pernicious, the following stage is to clean it out, which is where the new examination becomes an integral factor.
“When a danger is recognized, because of the effective idea of some horrendous malware, it is indispensable to have robotized activities to help with these discoveries,” continued Professor Burnap.
“We were spurred to attempt this work as there was nothing accessible that could do this sort of mechanized distinguishing and killing on a client’s machine progressively.”
Existing items, known as endpoint identification and reaction (EDR), are utilized to safeguard end-client gadgets like work areas, PCs, and cell phones and are intended to rapidly recognize, dissect, block, and contain assaults that are underway.
The principal issue with these items is that the gathered information should be shipped off to committees for a reaction to be carried out, by which time a piece of malware may as of now have caused harm.
To test the new discovery strategy, the group set up a virtual registration environment to address a gathering of ordinarily utilized PCs, each approaching 35 applications simultaneously to reenact an ordinary way of behaving.
The AI-based identification strategy was then tried, utilizing a great many examples of malware.
The lead creator of the review Matilda Rhode, presently Head of Innovation and Scouting at Airbus, said: “While we actually have a workable approach as far as working on the exactness of this framework before it very well may be carried out, this is a significant stage towards a robotized ongoing identification framework that wouldn’t just help our PCs and PCs, but additionally our savvy speakers, indoor regulators, vehicles, and fridges as the “Web of Things” turns out to be more prevalent.”





