As how much information is put away in gadgets and shared over the web constantly increments, PC researchers overall are attempting to devise new ways to deal with secure correspondence and safeguard delicate data. Probably the most deep-rooted and important methodologies are cryptographic procedures, which basically encode (i.e., change) information and messages traded between at least two gatherings, so only shippers and recipients can see it in its unique structure.
Actual unclonable capabilities (PUFs), gadgets that endeavor “arbitrary flaws,” are undeniably presented during the assembling of gadgets to give actual elements novel “fingerprints” (i.e., trust secures). Lately, these gadgets have ended up being especially important for making cryptographic keys, which are quickly deleted when they are utilized.
Peking University and Jihua Laboratory scientists have recently introduced another framework for creating cryptographic natives, which comprise two indistinguishable PUFs based on adjusted carbon nanotube (CNT) exhibits.This framework, presented in a paper distributed in Nature Electronics, could assist with getting correspondence more reliably, beating a portion of the weaknesses of recently proposed PUF gadgets.
Old-style cryptography utilizes cryptographic calculations and keys to encode or decode data, and the most famous systems are Rivest, Shamir, and Adleman (RSA) encryption, “Zhiyong Zhang,” one of the analysts who did the review, told TechXplore. “In an uneven calculation, the public key can be gotten to by anybody, yet the public key breaking requires figuring a huge number, which is very hard for an old-style PC.” This errand has, in any case, been shown numerically to be accomplishable in polynomial time utilizing a quantum PC.”
Perhaps one of the most utilized cryptographic systems today is symmetric encryption, which has something similar to “secret keys” for encryption and decoding with all clients partaking in a particular discussion. These systems, by and large, store secret keys in non-unstable memory, which is helpless against physical and side-channel digital assaults.
“We introduced a novel method, dual physically unclonable functions (PUFs), to achieve low-cost and hardware-based secure communication. The underlying idea behind PUFs is to employ random physical defects existing in a physical entity generated by small-scale fabrication process differences that cannot be predicted or copied, even by the original manufacturer.”
Zhiyong Zhang, one of the researchers
Lately, analysts have hence been investigating elective cryptographic methodologies, including quantum key dispersion (QKD). QKD strategies exploit ideas attached to the quantum hypothesis to safeguard correspondences. In particular, they influence the natural aggravations influencing quantum frameworks while they are being estimated.
QKD has been viewed as especially powerful at recognizing an outsider’s endeavors to get to the mystery key safeguarding interchanges. While some QKD systems have achieved amazing outcomes, they normally require modern and profoundly costly equipment.
“To accomplish minimal expense and equipment-based secure correspondence, we presented another innovation, twin truly unclonable capabilities (PUFs),” Zhang said. “The essential thought behind PUFs is to use irregular actual flaws existing in an actual element brought about by the creation cycle varieties on a limited scale, and these defects can’t be anticipated or cloned, even by the first maker.”
Because of their novel plan, PUF gadgets are unclonable and erratic. This makes them amazingly viable at creating safe mystery keys for encryption.
Regardless, when PUFs are utilized to get interchanges, the keys they produce should be composed on non-unstable recollections and imparted to other discussion members that don’t claim a PUF gadget. These put-away keys will hence be helpless against assaults.
The vital goal of the new work by Zhang and his partners was to beat this limit of PUF gadgets for getting interchanges. To do this, rather than cloning a current PUF, they attempted to make two indistinguishable (twin) PUFs.
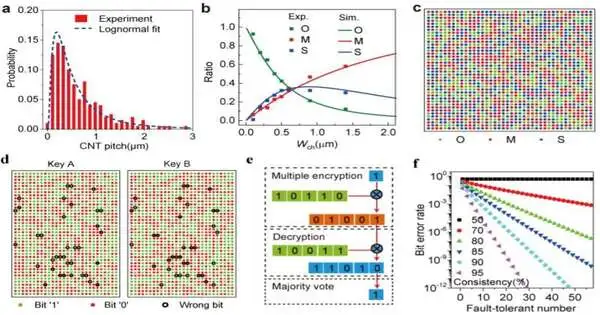
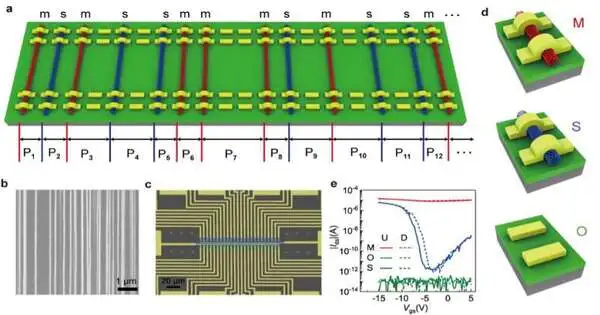
CNT twin PUF execution and demonstration of secure correspondencea, CNT throw distribution and information lognormal tantrumb, Ratios of three types of devices versus channel width of PUF devicesThe squares and lines address trial and recreation information separately. c, 1600 pieces of CNT PUF-produced ternary keysThe green, red, and blue circles address open (0,0), semiconducting (1,0), and metallic (1,1) pieces or gadgets separately. d, Twin paired-piece maps made from twin PUFs with two-fold parallel pieces.The strong green and strong red circles address bits ‘1’ and ‘0’, separately. The empty dark circles address in-steady or “wrong” bits. e, A diagram of secure correspondence using a problem-solving strategy.f, BER versus lenient number with different texturesZhong and colleagues
“We created twin truly unclonable capabilities (PUFs) in view of adjusted CNT exhibits,” Zhang made sense of. “We, right off the bat, became adjusted CNT clusters on quartz substrate. On one hand, incited by the quartz grid CNT connection, CNT exhibits became along the [2-1-1] gem direction for a few hundred microns, which guaranteed that the properties of CNT clusters were indistinguishable lined up with the development course. On the other hand, CNT exhibits irregular qualities like chirality and position, which are opposite to the CNT development course. “
To make their gadget, Zhang and his partners created two lines of field-impact semiconductors (FETs) on CNT exhibits. They utilized semiconductors with three channel types with various electrical properties, in particular channels containing some metallic CNTs (M), absolutely semiconducting CNTs (S) and no CNTs by any means (O).
“Because the area and type of CNTs are not fixed by stochastic nucleation and arbitrary impetus dispersion, FETs were created on the CNT exhibits,” Zhang explained.”In the mean time, two lines of FETs created in line up on a similar CNT cluster show O, S, and M sorts with a similar request, so two indistinguishable PUFs (twin PUFs) can be created together.”
Zhang and his partners first conceived a model that would permit them to concentrate on the connection between PUFs and both CNT exhibits and gadget aspects. This model permitted them to increase the irregularity and entropy of their PUFs.
“We found that the CNT pitches (CPs) meet the lognormal dispersion, which was checked by other CNT tests we developed with various densities and those distributed by different gatherings,” Zhang said.
Utilizing recreations and the model they made as a kind of perspective, the scientists enhanced their plan and made CNT exhibits with a CNT pitch of 0.650.58 m and a metallic/semiconducting CNT proportion of roughly 0.4. They then utilized these clusters to make a model of their PUFs with ideal ternary pieces.
“We created a sum of 1600 FETs with a channel width of 600 nm, to produce a 4040 ternary piece map, in which 532, 516, and 552 O-, S-, and M-pieces were counted separately,” Zhang said. “Our PUFs likewise showed high irregularity, consistency, uniqueness, unusualness, and dependability.”
In their tests, the analysts effectively utilized their twin PUFs to achieve issue-lenient cryptography. Because of flaws related to the development of the CNTs, including chirality changes, the presence of broken tubes between impetus stripes and misalignment, the group’s twin PUFs at first showed a non-wonderful consistency. This implies that the encryption and decoding cycles could present wrong pieces, which brings about a high Bit Error Rate (BER).
“To lessen the BER, we planned to issue lenient cryptography in which various key pieces (3, odd) are utilized to encode one plain text bit into numerous code text bits, and the different code text pieces are decoded and, afterward, create one plain text bit through a larger part vote,” Zhang said. “The BER was dramatically decreased, with an issue lenient number for consistency more than 80%. “In our twin PUFs with a consistency of 95%, the BER can be decreased to one out of many when the shortcoming lenient number depends on 29.”
Later on, the twin PUF gadgets made by this group of scientists could assist with getting interchanges more reliably for a huge scope. For their next examinations, Zhang and his partners might want to further develop their gadgets, for example, by enhancing the materials utilized in their new work.
“We intend to work on the cleanness of the quartz substrate and the wind stream security during CNT development, which can reduce the event of broken tubes and chirality change,” Zhang added. “In this paper we utilized a worldwide base door, yet we currently likewise plan to transform it to a top-entryway structure for little activity voltage and simple mixing with different circuits. At last, while up to this point we utilized a test station to test our PUF units individually, the next stage will be to coordinate our twin PUFs with fringe circuits, which can naturally understand the encryption of data.
More information: Donglai Zhong et al, Twin physically unclonable functions based on aligned carbon nanotube arrays, Nature Electronics (2022). DOI: 10.1038/s41928-022-00787-x
Journal information: Nature Electronics