Profound learning methods have as of late ended up being exceptionally encouraging for recognizing network safety assaults and deciding their tendency. Simultaneously, numerous cybercriminals have been conceiving new goes after pointed toward impeding the working of different profound learning devices, including those for picture order and normal language handling.
Maybe the most well-known among these assaults are ill-disposed assaults, which are intended to “fool” profound learning calculations utilizing information that has been altered, inciting them to mistakenly group it. This can prompt the failing of numerous applications, biometric frameworks, and different advances that work through profound learning calculations.
A few past examinations have shown the viability of various ill-disposed assaults in provoking profound brain organizations (DNNs) to make problematic and bogus forecasts. These assaults incorporate the Carlini and Wagner assault, the Deepfool assault, the quick slope sign strategy (FGSM) and the Elastic-Net assault (ENA).
“Much of the current work in the field of adversarial learning has been undertaken with a wide array of methods in image processing and natural language processing. The Elastic-Net Attack on Deep Neural Networks (EAD) and TextAttack are two techniques of interest.”
Jared Mathews
Scientists at the Citadel have as of late fostered a DNN that can identify a kind of cyberattack known as conveyed refusal of administration (DDoS) DNS enhancement, and afterward utilized two unique calculations to create ill-disposed models that could deceive their DNN. Their discoveries, distributed in a paper pre-distributed on arXiv, further affirm the shakiness of profound learning strategies for DNS assault location and their weakness to ill-disposed assaults.
DDoS DNS enhancement assaults exploit weaknesses of area name framework (DNS) servers to intensify the questions made to them, at last flooding them with data and cutting the servers down. These assaults can make huge disturbance online administrations, including those show to both little and large global organizations.
Throughout recent years, PC researchers have fostered a few profound learning methods that can identify DDoS DNS enhancement assaults. Regardless, the group at the Citadel demonstrated the way that these methods could be evaded utilizing ill-disposed networks.
“A large part of the ongoing work in the field of ill-disposed learning has been led in picture handling and normal language handling with a wide assortment of calculations,” Jared Mathews and his partners wrote in their paper. “Two calculations of interest are the Elastic-Net Attack on Deep Neural Networks (EAD) and TextAttack.”
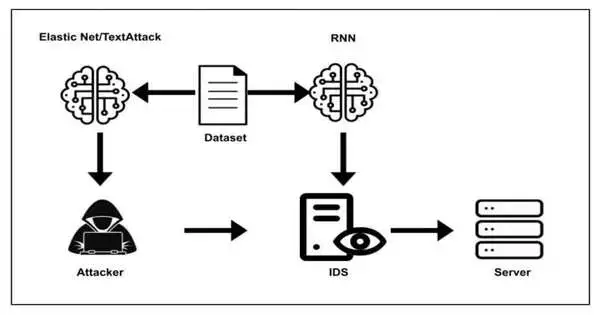
EAD and TextAttack are two calculations that have ended up being especially great at making altered information that would be misclassified by DNNs. Mathews and his partners hence fostered a method for recognizing DDOS DNS enhancement assaults and afterward attempted to trick it utilizing ill-disposed information created by the EAD and TextAttack calculations.
“In our trial the EAD and TextAttack calculations are applied to a Domain Name System enhancement classifier,” the scientists wrote in their paper. “The calculations are utilized to create noxious DDoS antagonistic guides to then take care of as contributions to the organization interruption location frameworks brain organization to group as legitimate traffic.”
In their tests, Mathews and his partners found that the ill-disposed information created by EAD and TextAttack could trick their DNN for DDoS DNS enhancement assault location 100 percent and 67.63% of the time, separately. These outcomes hence feature the huge defects and weaknesses of existing profound learning-based techniques for recognizing these assaults.
“We show that both picture handling and normal language handling ill-disposed learning calculations can be applied against an organization interruption location brain organization,” the scientists wrote in their paper.
Later on, the work by this group of analysts at the Citadel could move the improvement of additional viable devices for recognizing DDoS DNS enhancement assaults, which can identify antagonistic information and accurately order it. In their next examinations, the scientists intend to test the viability of ill-disposed assaults on a specific kind of calculations for identifying DNS enhancement assaults, those focusing on the supposed obliged application convention (CoAP) utilized by numerous IoT gadgets.
More information: Jared Mathews, Prosenjit Chatterjee, Shankar Banik, Cory Nance, A deep learning approach to create DNS amplification attacks. arXiv:2206.14346v1 [cs.CR], arxiv.org/abs/2206.14346