Lately, numerous cell phone clients have become worried about the protection of their information and the degree to which organizations could approach this information. As things stand today, the applications that clients can run on their telephones and how they can manage them are not entirely set in stone by a couple of large tech organizations.
Scientists at ETH Zurich have as of late set out on a mission to change this latest thing through the improvement of a new cell phone design called TEEtime. This engineering, presented in a paper pre-distributed on arXiv, permits clients to deftly pick which assets on their cell phone they will devote to heritage working frameworks, like Android or iOS, and which they wish to save for their own exclusive programming and information.
“This work was enlivened (to a limited extent) by our encounters in creating Swiss contact-following applications, where we immediately saw how restricted we are as scientists and designers in getting to a few fundamental administrations on ‘our’ telephones,” Srdjan Capkun, one of the specialists who completed the review, told TechXplore.
“This experience helped us realize that even state-run administrations need to haggle with conspicuous telephone operating system sellers (Apple and Google) to acquire explicit access, like Bluetooth radios. This model made us look all the more comprehensively at the limitations we face today on “our” cell phones, which have political and financial ramifications for residents, organizations, and legislatures.”
The absence of client command over assets on cell phones is ordinarily legitimated by working framework designers and telephone suppliers as a viable way to offer security and protection. One could argue that opening cell phone frameworks would endanger clients (i.e., increase their vulnerability to assaults) and have a negative impact on their overall route insight.
The vital goal of the new work by Groschupp et al. was to demonstrate the way that one might actually give clients more noteworthy command over their telephone while holding onto existing working frameworks with their functionalities and safety efforts. To do this, the group created TEEtime, a new cell phone plan design that permits different “spaces” running all the while to coincide on a cell phone.
“With TEEtime, we create simultaneously executing “spaces” that are safeguarded from one another, utilizing equipment highlights consolidated in current computer processors and stages,” Groschupp made sense of. “Clients can run a few spaces on their telephones, e.g., a full Android or iOS, with all the comfort and security that they give, and in equal measure, restrictive programming in another space.”
Basically, TEEtime confines various spaces, permitting clients to determine the degree to which every one of these areas approaches assets on their telephone. This implies that clients would be able, for example, to run a route application in their own disconnected space, giving GPS access just to this area and subsequently blocking Android and iOS from getting their GPS information. The equivalent should likewise be possible with different peripherals, like Bluetooth or the telephone’s in-built receiver and camera.
“The presentation of areas enjoys two primary benefits as far as giving clients command over their gadgets,” Groschupp made sense of. “It, right off the bat, gives clients full control of the protection of their information, for example, by permitting them to store their photographs in a different space, where the client can ensure that no client-side filtering is performed. Note that in current telephone biological systems, these highlights can be quietly presented without the client in any event seeing or having the likelihood to quit.”
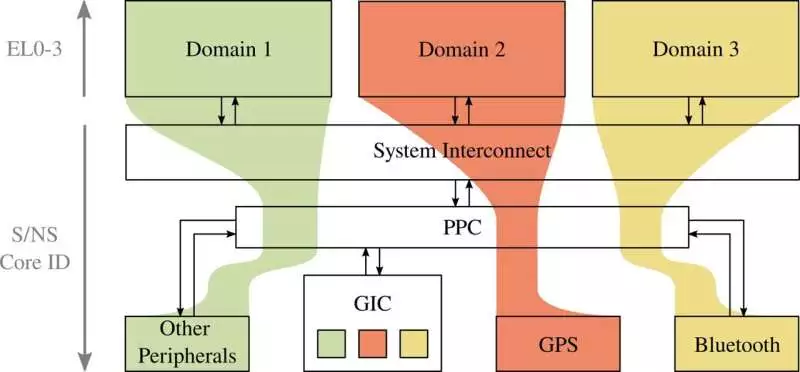
Undisputed level outline of space disengagement in TEEtime: Access to peripherals is supported by a parcel regulator (PPC).The hinder regulator (GIC) is divided into spaces so that all areas can deal with hinders affecting their peripherals.
The second benefit of the TEEtime design is that it can foreclose control or increase protection. As a result, if their working specialist co-ops obstruct or prevent them from introducing an application, they can still run it in another space.
Until now, the experts had tested a model of their engineering on an ARM emulator, a product device commonly used to test operating systems and other cell phone programming.These underlying assessments were promising, as they recommended that TEEtime functions admirably and doesn’t influence a framework’s security.
“We demonstrate that it is unquestionably possible to run programming that is frequently questioned on a single phone with existing native equipment,” Groschupp said.”We trust this prompts an adjustment of the public’s view of the cell phone biological system. Convenience, security, and client control are not fundamentally unrelated. A significant plan decision for us was to cease from utilizing hypervisors, as we needed to stay away from complex, highly favored programming on the telephones, since this would require again entrusting enormous business elements with their turns of events and updates.”
Later on, the design created by this group of specialists could be ready for the production of other programming arrangements that give clients more prominent control over their cell phones. Meanwhile, Groschupp and her associates intend to foster TEEtime further, to conquer constraints that might actually upset its huge scope of execution.
“Our desire is to foster a completely working telephone model and, through it, inspire telephone makers to help this plan,” Groschupp added. “We are at present chipping away at various leftover issues, incorporating protecting client cooperations with our framework, and examining changes to equipment that would simplify our answer for coordination and, surprisingly, be more productive.”
More information: Friederike Groschupp et al, It’s TEEtime: Bringing User Sovereignty to Smartphones, arXiv (2022). DOI: 10.48550/arxiv.2211.05206
Journal information: arXiv